在CentOS7上安装部署WireGuard
准备工作,需要enable ipv4的ip_forward转发功能:
sysctl -w net.ipv4.ip_forward=1
或者修改sysctl.conf文件
vi /etc/sysctl.d/sysctl.conf net.ipv4.ip_forward=1 sysctl -p #执行并生效
一 更新内核
安装kernel headers
这个根据系统版本来决定是否安装的,如果已经安装了它有提示,如果没有,安装成功后记得reboot一下
yum install kernel-headers-$(uname -r) kernel-devel-$(uname -r)
安装内核
wget https://www.cloudy.pub/down/files/kernel/centos7/kernel-ml-4.17.3-1.el7.elrepo.x86_64.rpm wget https://www.cloudy.pub/down/files/kernel/centos7/kernel-ml-devel-4.17.3-1.el7.elrepo.x86_64.rpm wget https://www.cloudy.pub/down/files/kernel/centos7/kernel-ml-headers-4.17.3-1.el7.elrepo.x86_64.rpm rpm -ivh kernel-ml-4.17.3-1.el7.elrepo.x86_64.rpm rpm -ivh kernel-ml-devel-4.17.3-1.el7.elrepo.x86_64.rpm rpm -ivh kernel-ml-headers-4.17.3-1.el7.elrepo.x86_64.rpm reboot
二 安装WireGuard
在安装完wireguard相关模块后记得需要重启一下。
curl -Lo /etc/yum.repos.d/wireguard.repo https://copr.fedorainfracloud.org/coprs/jdoss/wireguard/repo/epel-7/jdoss-wireguard-epel-7.repo yum install epel-release yum install wireguard-dkms wireguard-tools modprobe wireguard
三 生成密钥
mkdir /etc/wireguard wg genkey | tee /etc/wireguard/privatekey | wg pubkey > /etc/wireguard/publickey
如果你觉得写入到两个文件中太麻烦,我们可以生成到一个文件里面
wg genkey | tee tempkey | wg pubkey >> tempkey
cat tempkey,可以看到两行密钥,第一行是privatekey,第二行是publickey
四 配置服务端
通过 vi /etc/wireguard/wg0.conf,添加以下内容
[Interface] PrivateKey = <Private Key> Address = 192.168.2.1/24, fd86:ea04:1115::1/64 ListenPort = 51820 PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE; ip6tables -A FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -A POSTROUTING -o eth0 -j MASQUERADE PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE; ip6tables -D FORWARD -i wg0 -j ACCEPT; ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE SaveConfig = true
最近更新,配置了多客户端的配置文件
[Interface] Address = 192.168.2.1/24 PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE ListenPort = 51820 #设置端口 PrivateKey = <----server privatekey-----> [Peer] PublicKey = <----client1 privatekey-----> AllowedIPs = 192.168.2.3/32 #注意这里子网掩码的配置,是32不是24 [Peer] PublicKey = <----client2 privatekey-----> AllowedIPs = 192.168.2.5/32
有防火墙记得给相应端口放行
#Option 1
vi /etc/firewalld/services/wireguard.xml
<?xml version="1.0" encoding="utf-8"?> <service> <short>wireguard</short> <description>WireGuard (wg) custom installation</description> <port protocol="udp" port="51820"/> </service>
firewall-cmd --zone=public --add-service=wireguard --permanent firewall-cmd --zone=public --add-masquerade --permanent firewall-cmd --reload firewall-cmd --list-all
#Option 2
firewall-cmd --add-port=51820/udp firewall-cmd --list-ports firewall-cmd --reload
#Option3
firewall-cmd --permanent --add-rich-rule='rule family=ipv4 source address=10.200.200.1/24 masquerade' firewall-cmd --permanent --direct --add-rule ipv4 filter FORWARD 0 -i wg0 -o eth0 -j ACCEPT firewall-cmd --reload
五 WireGuard服务管理
启动服务
wg-quick up wg0
关闭服务
wg-quick down wg0
设置随机自启动
systemctl enable wg-quick@wg0
查看连接状态
wg
添加peer配置信息
wg set wg0 peer <Client Public Key> endpoint <Client IP address>:<Server Port> allowed-ips <IP>
保存wg0.conf的peer配置信息
wg-quick save wg0
删除peer配置信息
wg set wg0 peer <!---客户端publickey----> remove
#Option
chown -R root:root /etc/wireguard/ chmod -R og-rwx /etc/wireguard/* systemctl enable [email protected] systemctl start [email protected] systemctl stop [email protected]
六 客户端配置
WireGuard是双向验证的,在服务端生成出的publickey在客户端中需要绑定验证,同样在客户端中生成的publickey也需要在服务端绑定验证。
Android
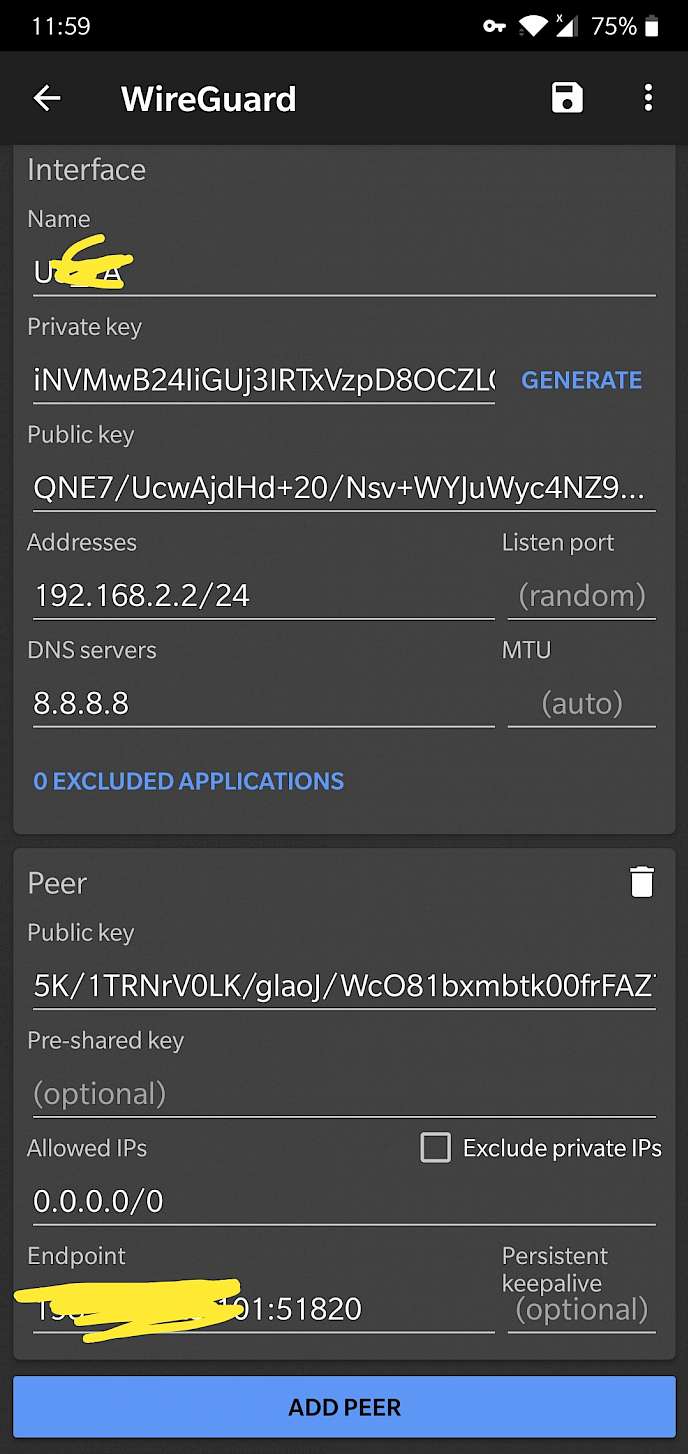
验证的两种方式
1. 使用wg命令
wg set wg0 peer <Client Public Key> endpoint <Client IP address>:51820 allowed-ips 192.168.2.2/24,fd86:ea04:1115::5/64
这里的allowed-ips参数建议设置成0.0.0.0/0; 由于上面服务端的wg0.conf中我们设置了SaveConfig = true这个参数,所以在执行完这个命令之后wg0.conf配置文件会自动加入客户端的配置信息,如
[Peer] PublicKey = <*******key**********> AllowedIPs = 192.168.2.0/24 Endpoint = 117.82.187.245:15040
2.在客户端端wg0.conf中配置[peer],加入服务端的信息使用public key, public IP地址和port.
[Peer] PublicKey = <Server Public key> Endpoint = <Server Public IP>:51820 AllowedIPs = 192.168.2.1/24, fd86:ea04:1115::1/64
REF